Be Prepared to Neutralize Cyberattacks When – Not If – They Happen
Businesses today are under the constant threat of cyberattacks from ransomware and extortion. In fact, 68% of business leaders feel their risk of a cyberattack is increasing, according to Accenture.
For years, enterprise-level organizations have relied on data protection platforms focusing solely on prevention and detection for protection against cyber threats. What they’re missing is the ability to build immunity against attacks.

To build immunity, you must accept the fact cybercriminals will break into your systems to steal valuable data or freeze critical systems. It’s no longer a question of “if” you will experience a breach. Instead, it comes down to “when” and how bad it will be for you and your customers.
These days, it’s critical to minimize or eliminate an attacker’s leverage and neutralize the potential damage.
Why Do Cyberattacks Happen?
Know What Motivates Your Attacker
To neutralize the damage and protect against cyber attacks and data breaches, you must first understand what motivates your attacker.
Cyberattackers have three goals that every defense strategy must anticipate. They include:
- Theft of valuable data and intellectual property, which can be sold to competitors or shared online.
- Extortion for monetary gain commonly associated with Ransomware attacks.
- Disruption of critical operations normally by state-sponsored attacks to inflect physical, political, psychosocial, economic, or other damage.
How Can You Prevent a Cyberattack?
Create a Three-Prong Line of Defense
To eliminate the chances of cybercriminals from achieving these goals, you need to bolster defenses along these three lines:
- Ensure your valuable data or IP cannot be stolen.
- Make exfiltrated data ineffective for extortion.
- Provide for immediate restoration of disrupted services.
Chances are you have the third step covered with automated backup services or cloud-based disaster recovery to restore your systems and data in the event of a cyberattack.
Unfortunately, most companies neglect steps 1 and 2. That’s because ransomware and extortion actors create the most damage before you know they’re inside your systems. By this time, attackers can take large amounts of your sensitive data, holding tremendous leverage over your business and customers.
Most cyberattacks gain entrance with legitimate credentials to unlock encryption-at-rest, which enables data to be exfiltrated in clear text, causing massive damage to a company’s security, privacy, compliance, and customer trust.
What Does a Cyberattack Look Like?
The attack strategy looks something like this:
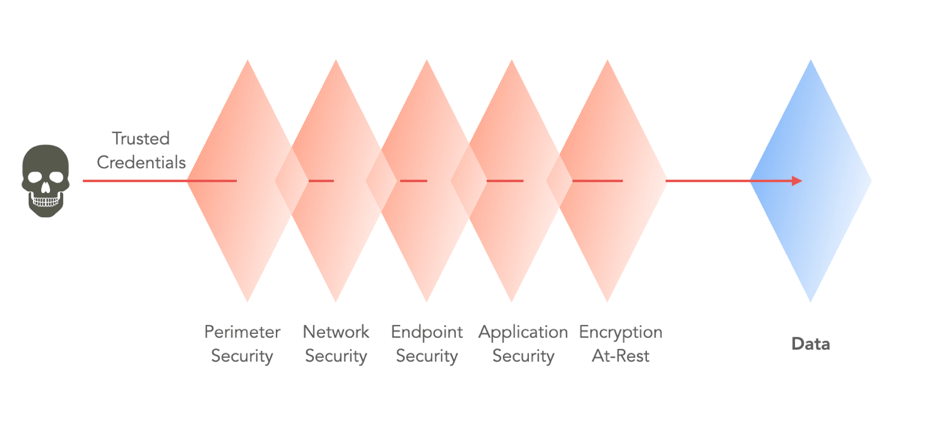
Attackers use clear text-sensitive data to demand ransoms. Even if you’re fully capable of restoring systems from backup, you might still pay the ransom to avoid data leakage, partner and customer extortion, the sale of secrets to competitors, and posting private data online. Even then, there is no guarantee your data will remain uncompromised.
Defense Against a Cyberattack
Portal26 protects systems by utilizing encryption-in-use to create a layer of protection in front of your data that doesn’t yield to clear text, even if the attack uses the highest privilege credentials.
With Portal26, your data security looks like this:
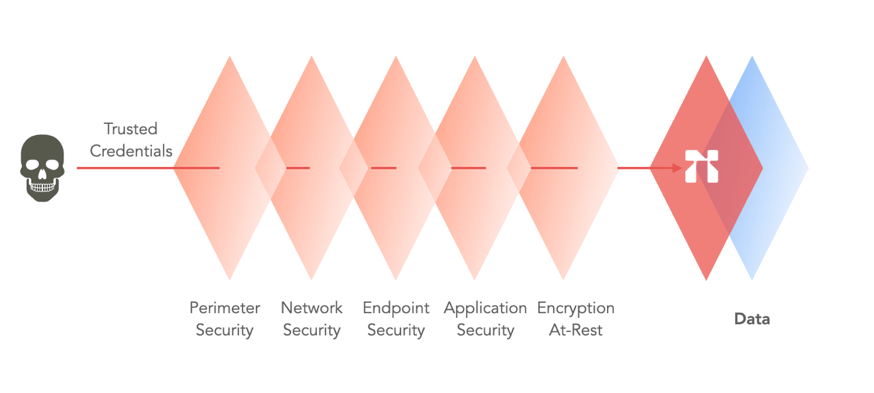
The data security platform combines encryption-in-use, traditional encryption, private data release, customer-controlled keys, and enterprise-wide key orchestration that allows data to remain secure throughout its lifecycle and as it moves across the enterprise.
Our encryption-in-use retains full use of data by separately encrypting the source data and then constructing an encrypted search index based on pre-declared search types.
Portal26 offers traditional and format-preserving encryption, tokenization, redaction, and masking. Data inside Portal26-protected systems is always encrypted. These additional formats can be utilized for private and secure data release.
Portal26 protection is offered at all levels of data collection, including overall collection, index, document, and granular field level. All Portal26 products offer key control functionality that enables granular keys to be customer-owned and controlled. Customer-controlled keys do not reduce system functionality.
Portal26 provides field-level auditable certification that protects data with retained NIST-certified encryption during an attack, including data that is observed, accessed, or exfiltrated.
To learn more about the Portal26 approach to data security and our data protection platform, schedule a demo today.
Related Resources
Black Swan in Data Security
Black Swan In Data Security A few years ago, I read the book Black Swan by Nassim Nicholas Taleb. The primary thesis is that we

Normalizing Outliers in Cybersecurity – Ransomware Edition
Ransomware Defense: Normalizing Outliers in Cybersecurity – Ransomware Edition Last week, I wrote an article titled “Black Swan in Data Security”. The primary point I
Data Exfiltration And How To Protect Your Data
Essential Data Protection Strategies: How to protect against Data Exfiltration Portal26’s ‘State of Data Exfiltration & Extortion Report’ shows that organizations may be less protected
