IDC Report. Written by: Jennifer Glenn, Research Director, Security and Trust
Enterprise Security Protecting the Digital Enterprise Requires a Multifaceted Data Security Platform
The digital economy puts new pressure on security and privacy teams to protect data while keeping it available. A data security platform helps organizations balance these two critical elements while speeding time to value.
Learn how Portal26 consolidates multiple data security techniques into a single platform thus improving cost, efficiency and value – making it easier to balance usability, security, and cost.

Disclaimer: This publication was produced by IDC Custom Solutions. The opinion, analysis, and research results presented herein are drawn from more detailed research and analysis independently conducted and published by IDC, unless specific vendor sponsorship is noted. IDC Custom Solutions makes IDC content available in a wide range of formats for distribution by various companies. A license to distribute IDC content does not imply endorsement of or opinion about the licensee. External Publication of IDC Information and Data — Any IDC information that is to be used in advertising, press releases, or promotional materials requires prior written approval from the appropriate IDC Vice President or Country Manager. A draft of the proposed document should accompany any such request. IDC reserves the right to deny approval of external usage for any reason.
Introduction
 Digital transformation is no longer on the horizon — it’s here. In IDC’s February 2023 Future Enterprise Resiliency and Spending Survey, Wave 1, 15% of organizations identified as a digital-native business, and 37% of organizations identified as a mostly digital business.
Digital transformation is no longer on the horizon — it’s here. In IDC’s February 2023 Future Enterprise Resiliency and Spending Survey, Wave 1, 15% of organizations identified as a digital-native business, and 37% of organizations identified as a mostly digital business.
The transformation to a digital business has changed the way organizations interact with their employees, partners, and customers. This shift has made data more portable and functional across multiple business use cases. Enterprise data may now live on multiple clouds or inside SaaS applications. An organization’s customer or operational data may also reside in on-premises or cloud databases or on a private cloud.
This level of data proliferation means the amount of data being generated and shared across the organization has increased exponentially. In IDC’s December 2022 Data Privacy Survey, 42% of respondents said they expect their data volume to increase by 25% or more over the next three years.
So, what you have is a massive amount of data, spread in more places and used for more operations. Data is unlike most tangible assets in that an increase in the amount of data doesn’t decrease its value. In fact, the opposite is true. Data is, arguably, the most valuable asset in the digital enterprise. The information in business data underpins essential operations and serves as the foundation for customer-facing experiences.
Attackers understand the value of data to the business and its customers, which is why attacks, such as ransomware, that block access to data and steal data, can be detrimental to the organization’s operations. These attackers may also use the chaos of a ransomware attack to hide exfiltration activity. Once data is exfiltrated, the threat of leaking the data is used to extort victims. External attacks are not the only concern for organizations. Insiders pose a tremendous risk to the security and protection of the organization’s most valuable information. Whether the exposure of data is the result of malicious intent on the part of insiders or a byproduct of misconfigured controls, it can have tremendous consequences for the organization.
While all data is important to the business, the value of sensitive or confidential data is incredibly significant. This data has tremendous worth to attackers and malicious insiders looking to sell information or extort the company, and exposure of sensitive or confidential data can result in expensive consequences, including noncompliance fines, lost business, and legal costs.
Balancing Data Security with Usability
It’s clear that digital data is a fundamental and portable building block for enhancing the customer experience through customized user interfaces and applications to more efficient back-end processes that improve delivery and service. Despite this, organizations are struggling to share this data throughout the different departments. In IDC’s February 2023 Future Enterprise Resiliency and Spending Survey, Wave 1, only 12% of respondents said they connect customer data between departments.
One of the most significant challenges with sharing this data, as reported in the same survey, is security. As Figure 1 illustrates, 21% of respondents highlighted security as their biggest process and automation challenge in sharing customer data across the organization. However, 18% cited compliance needs and regulatory concerns as their biggest data management and governance challenge. These numbers show just how much of a balancing act today’s businesses are performing to keep data secure and protected while keeping with the spirit of the digital economy — that is, data that is instantly available to and usable by the applications, devices, and users that require it.
FIGURE 1: Organizations Are Struggling to Share Data Appropriately (% of Respondents)
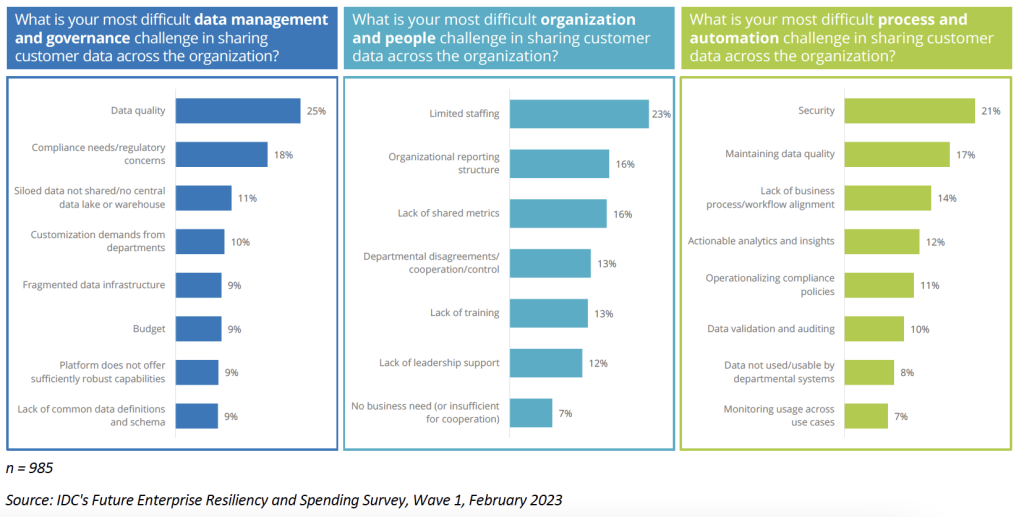
Given the sheer enormity of protecting all data, most companies have focused efforts in the past several years on securing confidential and sensitive information. This type of data can include everything from security-related content such as intellectual property and business financials to personal identifiers and customer information. In either case — security or privacy — confidential or sensitive data requires extra controls to prevent unauthorized access and/or exfiltration.
For many organizations, this has been a clear problem for years, and they have invested heavily in multiple types of data technologies to address it. Figure 2 shows the scope of technologies that teams are using to protect sensitive or private data from being accessed inappropriately: data loss prevention (DLP), data classification, data access governance (DAG), masking, tokenization, and encryption and key management. Survey respondents reported using these traditional “security” technologies with a high level of success in addressing privacy requirements in their organizations.
FIGURE 2: Data Privacy Tool Effectiveness (% of Respondents)
Q How effective are these tools at addressing data privacy needs at your organization?
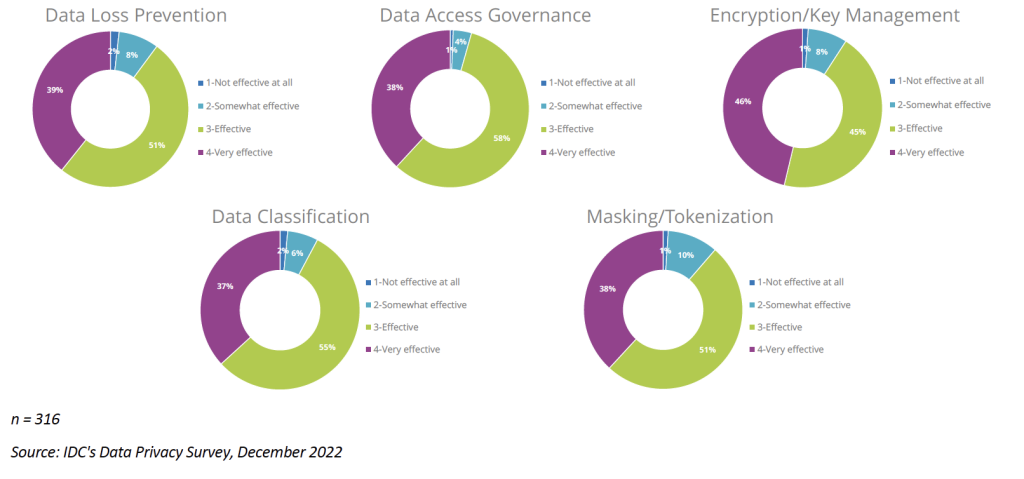
While customers have indicated these tools are effective in helping protect data, there are a few areas of concern. First, they are not always easy to use. Tuning DLP and DAG policies to be effective can be tedious. Additionally, running multiple technologies requires extra management and user involvement to consistently enforce security policies across each. Second, running multiple technologies requires budget and skilled human resources — both of which are in short supply in times of economic uncertainty. Further, many of these technologies are aimed at data at rest or data in motion.
So, how do companies confidently ensure sensitive data is protected while keeping it available to and usable by the right entities? The answer to this question often includes a mix of data security technologies that anonymize and/or obfuscate sensitive data so that even if it does fall into the wrong hands, it remains unreadable. This mix includes encryption, tokenization, masking, and other types of anonymization. It also involves searchable encryption, which enables full use of sensitive data including searching and analyzing it while keeping it encrypted.
Considering a Multitool Platform for Data Security
While encryption and obfuscation technologies close a gap in data security and privacy, particularly for data in use, managing several individual point solutions is incredibly complex. By combining multiple data security functions into a single platform, organizations can gain better visibility into and control over all of the data in their purview, instead of digging into specific applications and data sources. This level of visibility offers organizations numerous benefits, including:
» Improved integration. Security tools often need to share data to be most effective. This can pose a challenge for teams that are understaffed or resource constrained because pulling this information together becomes its own job. In a platform, data security tools are often designed to work together without the need for a separate integration. This eliminates — or at the very least reduces — the need for dedicated staff for this purpose.
» Consistent policy enforcement. One of the biggest challenges of managing multiple security tools is implementing enforcement consistently for each product or service. Often, these tools do not function or show information in the same way, so blanket policies are difficult — if not impossible — to enforce. A single platform offers the opportunity for uniform policy enforcement, which is easier to manage and helps improve overall security posture.
» Faster time to value. Removing the need to integrate information from multiple tools makes it easier to demonstrate compliance with data security or data privacy requirements. Plus, removing extraneous licenses and limiting the number of resources required for management boost ROI.
» Reduced cost. Managing the integrations between different tools is both complex and resource intensive, which means it can also be expensive. A platform featuring multiple data security tools eliminates these integration requirements, helping keep costs in check.
Considering Portal26
Portal26 was founded in 2019 and has built a multifaceted data security platform that is designed to help organizations address the following critical gaps in their data protection:
» Security for data in use. Securing data in use prevents attackers from viewing data even if they have privileged credentials. Searchable encryption from Portal26 attaches to data sources and repositories, including databases, enterprise search platforms, file shares, and applications. It is designed to allow organizations to run queries, conduct analytics, or aggregate data without having to decrypt it. This means that attackers or malicious insiders cannot view or access data after it has been exfiltrated.
» Comprehensive controls for unified security and privacy enforcement. Beyond encryption in use, the Portal26 platform includes a deep portfolio of security and privacy controls, all of which can be managed from a single engine. The platform offers granular controls based on role-based access, designed to help organizations ensure only the right entities — users and/or applications — can access unencrypted data. These controls include searchable encryption as well as vaulted and vaultless tokenization, traditional and format preserving encryption, whole or partial data masking and redaction, hashing, and various types of anonymization.
» Multiple interoperable modules to support all types of architectures. The Portal26 platform consists of six modules that offer a range of data security technologies that work in the cloud, on premises, or in hybrid environments. Portal26 Vault, Search Plugin, Object Store Proxy, File Share Proxy, Translation Service, and Studio can attach to all types of databases, enterprise search platforms such as Elasticsearch and OpenSearch, object stores such as AWS S3 and Azure Blob, and file shares. It is designed to allow organizations to securely process and share data. It also helps secure new applications from the start.
» Owner-controlled key management. The Portal26 platform allows organizations to maintain ownership and control over their cryptographic keys, offering both bring your own key (BYOK) and hold your own key (HYOK) options. This capability is intended to help organizations that have data hosted/processed outside their control keep the encryption keys in a key vault, which can be accessed in real time to allow that data to be used.
» Proof of protection. The Portal26 platform is designed to help businesses with their regulatory audits. One of the core capabilities of the platform is a reporting feature that shows how sensitive or confidential data was kept encrypted even if the business was breached.
Addressing data security concerns is not a simple endeavor. To help customers, Portal26 has created solutions that build on one another. This buildable capability, combined with prebundled technology packages for common use cases, is designed to help organizations quickly and easily start addressing their biggest data security challenges.
Challenges
The Portal26 platform offers several data security capabilities in a single platform. While there are various benefits to this approach, it can be a tough sell to organizations that have already invested in individual technologies and the resources to run them. Further, while many organizations consider a platform solution an “ideal,” buyer behavior continues to lean toward individualized solutions, which enable a more bespoke experience. Still, Portal26’s incremental approach will serve the company well as it helps organizations slowly replace these technologies as they come up on their renewal.
Organizations must ensure that only the necessary data is usable, when it is needed and only by the right devices, applications, and users.
Conclusion
Protecting data is complicated because data is complicated. In the digital world, data is currency. It has tremendous value, not only for the organization but also for malicious actors who want to access and use it. Digital businesses walk a fine line between protecting the integrity of their most critical information and keeping that information available for use. Whether customer information, employee data, or intellectual property, organizations must ensure that only the necessary data is usable, when it is needed and only by the right devices, applications, and users. Being able to see and manage the accessibility of data from a single platform is critical in balancing data security and usability.
About the Analyst
Jennifer Glenn, Research Director, Security and Trust
Jennifer Glenn is Research Director for the IDC Security and Trust Group and is responsible for the information and data security practice. Ms. Glenn’s core coverage includes a broad range of technologies such as messaging security, sensitive data management, encryption, tokenization, rights management, key management, and certificates. |
More About Portal26Portal26 is an award-winning converged data security platform that provides the industry’s most advanced and comprehensive set of security and privacy controls in a single solution. From cutting-edge encryption-in-use and searchable encryption to all types of tokenization, traditional and format-preserving encryption, masking, anonymization and key-based controls, Portal26 enables enterprises to cut costs while still meet the enormous challenges posed by ransomware, “extortionware”, insider threats and complex data privacy regulations. Popular use cases include replacing traditional data tokenization solutions to enable rich analytics without detokenization, securing enterprise search, securing file servers from data breach, simplifying compliance, securely sharing sensitive data, enabling SaaS companies to let customers bring or hold their own keys (BYOK/HYOK), and enabling cross-border data privacy. Portal26 can be used for new applications or with existing architectures via interoperable modules such a fully encrypted analytic data vault, search plugin, proxy for object stores and file shares, and stand-alone translation service. Portal26 is NIST FIPS 140-2 certified. |

