Portal26 Ransomware Research Report: State of Data Exfiltration and Extortion
Portal26’s State of Data Exfiltration & Extortion Report for 2022 finds that with attackers winning over 60% of the time, enterprises seeking to defend themselves from ransomware and extortion, need to look beyond the current crop of prevention, detection, and backup solutions.

Executive Summary
With ransomware and related extortion fast becoming the biggest cybersecurity risk for both enterprises and governments, organizations are looking to actively bolster their defenses and minimize the impact from such attacks. The last eighteen months have seen hundreds of millions of dollars invested in traditional prevention, detection, and backup solutions, with the hope that these will help mitigate the impact from ransomware attacks.
A look at the news headlines over the last year and all anecdotal evidence, however, suggests otherwise. From everything we can tell by digging into the news as well as talking to impacted organizations, the majority of them have not managed even a moderate level of success against this type of attack. Time and time again, companies with major investments in ransomware detection solutions are successfully brought down. Despite fully operational backup and recovery solutions, these companies find themselves so compromised that their only option ends up being the ransom payment as demanded by attackers.
At Portal26, we know that prevention, detection and backup are only part of the solution. We believe that the complete solution includes a strong focus on data security so that attackers are unable to gain leverage over victims through stolen data. Unless the data exfiltration vector is addressed, organizations will find themselves in a losing position despite all their other security investments. Portal26 has built a solution for this. We offer a cutting edge data security platform that combines traditional data protection techniques with high-performance encryption-in-use that effectively shuts down the large scale data exfiltration vector that is part and parcel of the modern ransomware attack.
We believe that the key to sharing our value proposition with CISOs and Boards is to base it on a strong data driven foundation. For this reason, we requested an independent research organization, CENSUSWIDE, to conduct a study.
Our study aimed to gather raw data on ransomware attacks, data exfiltration, extortion, ransom payments, prior investments in security, as well as forward looking budget priorities. Respondents included 107 Security Professionals in a variety of enterprises across the United States.

We also gathered data on security investments and budgets. Ultimately, the data showed that strong data security that protects against exfiltration and extortion is an enormous and critical need in the fight against ransomware.
Summary of Study Participants
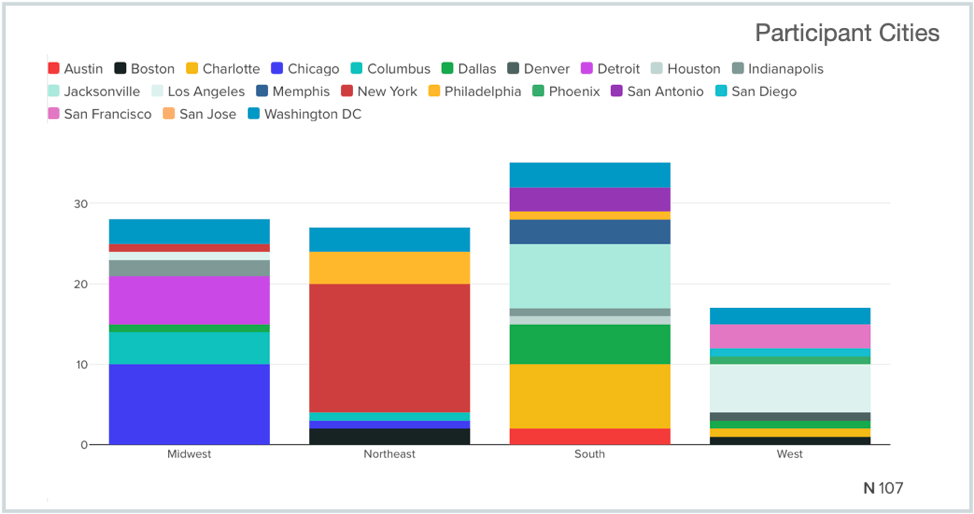
Portal26’s State of Data Exfiltration and Extortion Study included 107 participants across the United States from a variety of industries. Participants were all Security professionals. We requested a wide distribution cross regions and cities and participation definitely reflected this. See chart below for geographical spread of our participants.
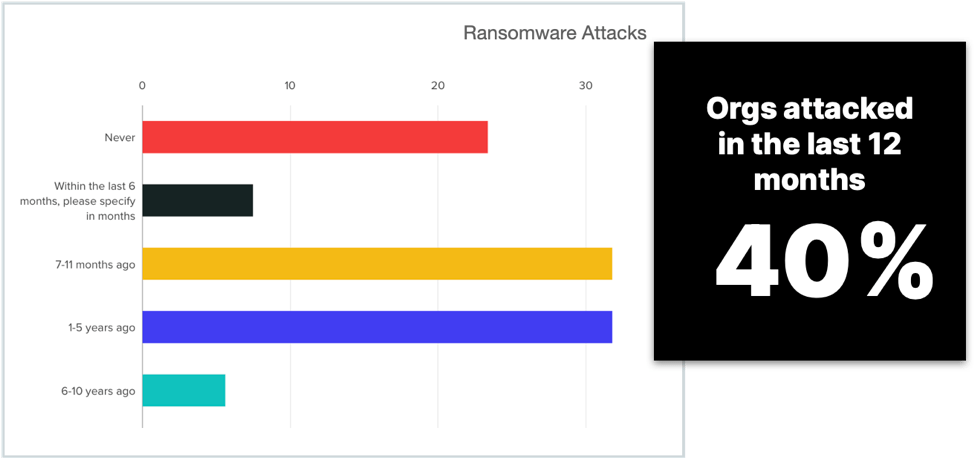
High Incidence of Ransomware Attacks
The study found that over 71% of respondents had experienced a ransomware attack in the last 5 years and over almost 40% in the last 12 months. This confirmed other research studies as well as our own anecdotal understanding of the extent of the ransomware problem. The chart below shows % out of a total of 107 responses.
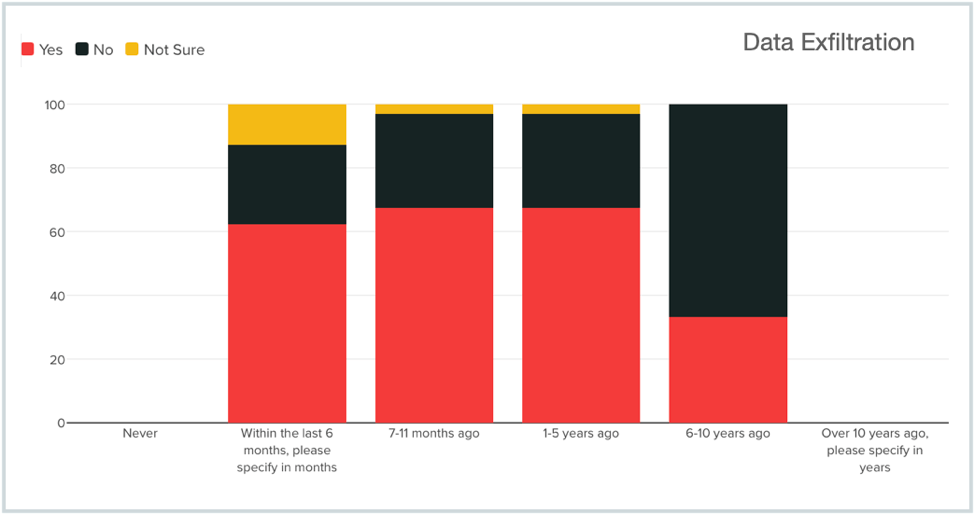
Majority of Attacks Involve Data Exfiltration
With the red bars in the chart below depicting the percentage of companies that had their data exfiltrated as part of the ransomware attack, it is clear that the nature of attacks has changed to include data exfiltration in a majority of the attacks. The data shows that while prior to 5 years ago, only 33% of attacks included data exfiltration, in recent years this number has grown to 68%.
Ransomware Attacks Have Evolved From 2-Stage to 3-Stage Attacks
This data above shows very clearly that ransomware attacks have gone from primarily two-stage attacks to primarily three-stage attacks. The original two stage attacks involved:
Stage 1: Infiltration and lateral movement to identify high value services, resources/data
Stage 2: Encryption of valuable services, resources, and data with the intent to extort
The original two-stage attack was well addressed by a combination of prevention/detection solutions and backup/recovery tools. If attackers were successful with Stage 2, organizations could recover from backup and ignore ransom demands.
Modern ransomware attacks are three-stage attacks with data exfiltration being the middle stage that provides unbeatable leverage for attackers. Data stolen in Stage 2 is used to extort victims even if they stand up impacted services and data from backup.
Stage 1: Infiltration and lateral movement to identify high value services, resources/data
Stage 2: Exfiltration of data with the intent to extort victims, customers, and partners
Stage 3: Encryption of valuable services, resources, and data with the intent to extort
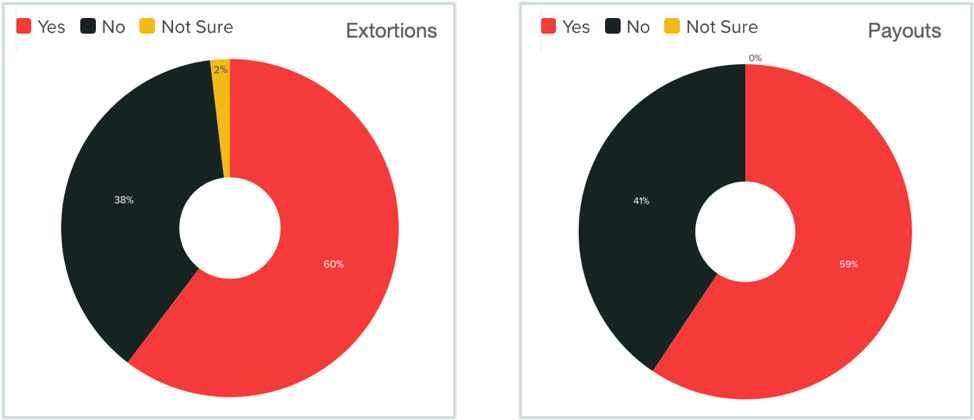
The study found that in the majority of cases where data was exfiltrated as part of the ransomware attack (60%), attackers then proceeded to extort the victims. This is consistent with what we learned from other studies as well as anecdotal conversations from ransomware victims. The data also shows that there are simply not enough protections in place from a data security point of view. A majority of those extorted (59%) found that the stolen data gave attackers unbeatable leverage and they ended up giving in to the ransomware demands presented to them.
 Stolen Data is used to Extort Victim Who are Forced to Pay
Stolen Data is used to Extort Victim Who are Forced to Pay
The study found that in the majority of cases where data was exfiltrated as part of the ransomware attack (60%), attackers then proceeded to extort the victims. This is consistent with what we learned from other studies as well as anecdotal conversations from ransomware victims. The data also shows that there are simply not enough protections in place from a data security point of view. A majority of those extorted (59%) found that the stolen data gave attackers unbeatable leverage and they ended up giving in to the ransomware demands presented to them.data exfiltration report
Demand for a Platform that Secures Data from Ransomware is Very High
The study also found that data was exposed and lost by means other than ransomware related data exfiltration. 47% of respondents across the board reported data exposure via other means.
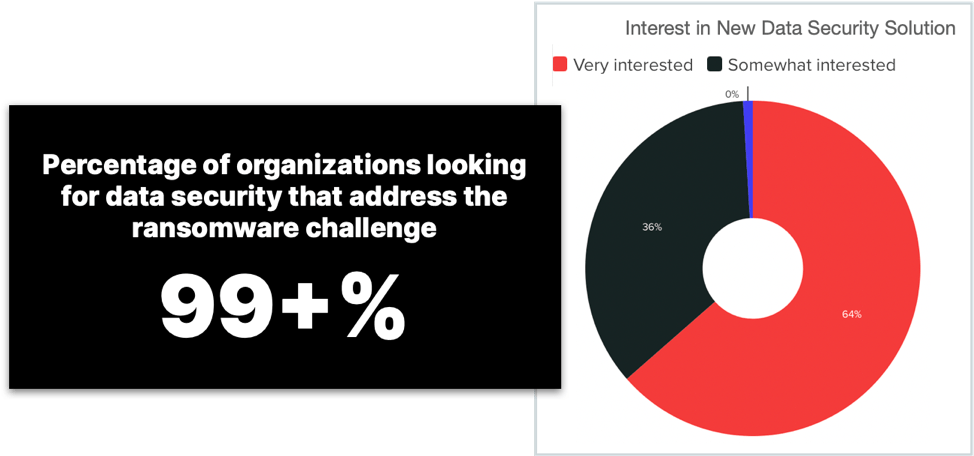
Regardless of how data was lost, over 99% of all participants expressed an interest in a data security platform that eliminates the loss of valuable data with 64% being very interested.
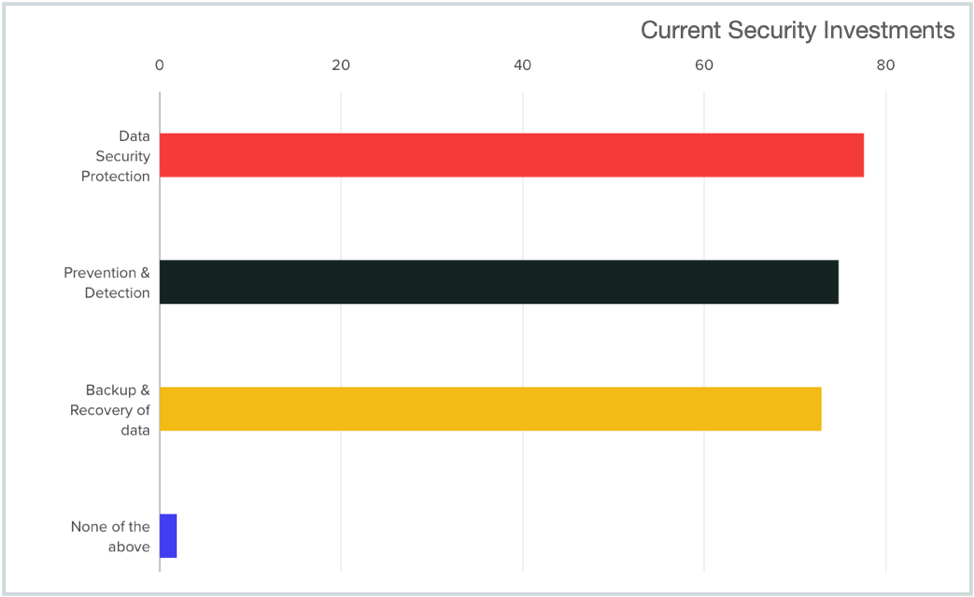
Current Security Solutions in Use
Study participants revealed strong investments in traditional technologies and we found an even spread between solution categories such as Prevention/Detection Solutions, Backup/Recovery Solutions, and Traditional Data Protection Solutions. See the chart below for the data that was gathered.
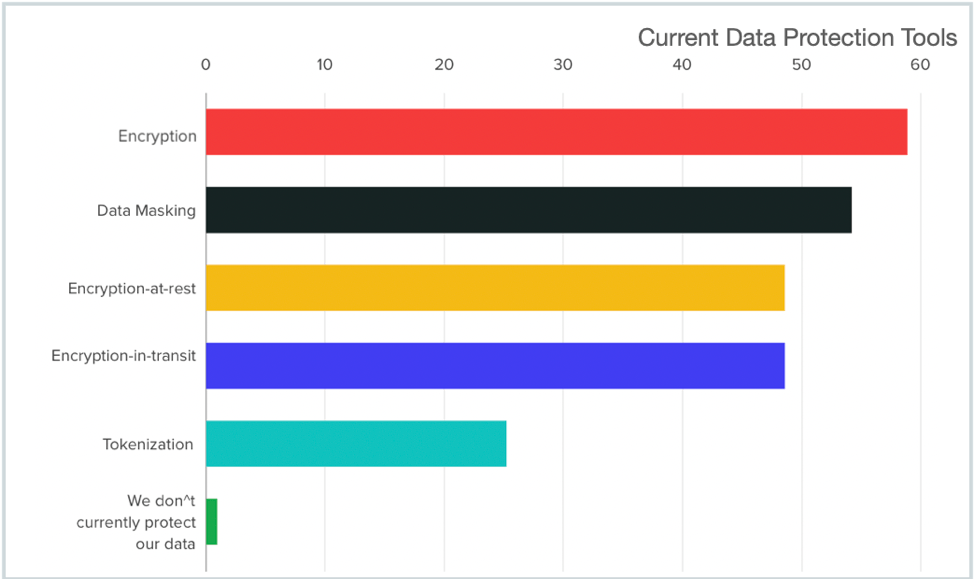
Within Data Protection, the study found that participants were utilizing all popular traditional data protection techniques. While their presence did not result in a good success rate against ransomware and data related extortion, having this data leads us to conclude that enterprises continue to make strong efforts to protect themselves and as they are introduced and adopt more effective solutions, they will see improved defense.
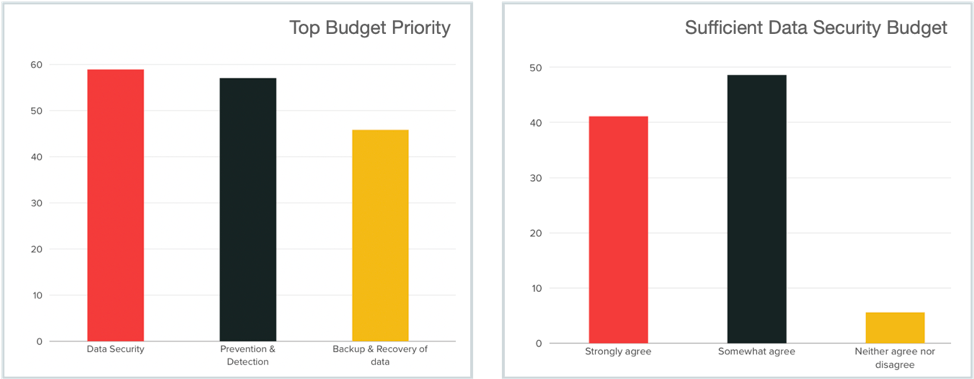
Data Security Budgets
The Study found very strong budgets for data security. Data Security was ranked as the top budget priority for 59% of responders compared to Prevention/Detection (56%) and Backup/Recovery tools at (47%). When asked whether they believed they had sufficient Data Security budget, a majority of respondents (90%) answered in the affirmative with 41% agreeing very strongly and 49% somewhat agreeing.
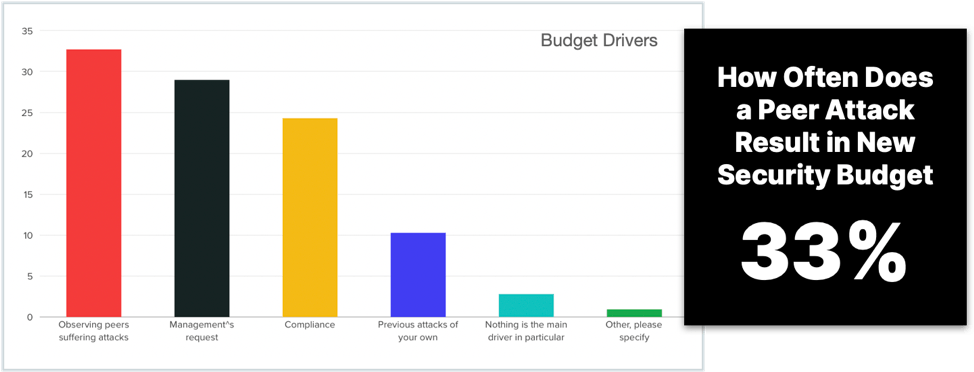
Our final question in the study asked participants to share what their primary data security budget drivers were and the answers were in line with our anecdotal experiences. The biggest factor driving purchase appears to be witnessing peers suffer ransomware and extortion attacks. This is followed by management requests, compliance considerations, and past ransomware attacks within their own organizations. Based on this data we should expect to see a lot more investment in Data Security Platforms that address the specific exfiltration and extortion challenges presented by modern ransomware attacks.
Conclusion
In conclusion the State of Data Exfiltration and Extortion 2022 study finds that current methods of data protection fall short of what is needed to stand up to the types of cyberattacks organizations are faced with today. The data shows that: while 75% of surveyed organizations deployed the full spectrum of tools covering prevention, detection, backup, recovery and traditional encryption technologies, we still saw that a massive 70% were successfully breached. 80% of surveyed organizations had encryption at rest and in transit in place and still an enormous 68% lost data in clear text Finally, when 70% of surveyed organizations had backup and recovery systems in place, 60% still ended up paying the ransom. These numbers highlight the big gap that still exists.
Learn More About Portal26’s Award Winning Data Security Platform
Portal26’s award winning data security platform combines high-performance encryption-in-use with nine traditional data security techniques to deliver immunity to data focused attacks.
Portal26 is a 2022 Gartner Cool Vendor, we are also in the 2022 Gartner Hype Cycle for Data Security and the 2022 Hype Cycle for Data Privacy. Portal26 is a 2022 SINET16 security innovation award winner (elected by 117 F500 CISOs and Chief Risk Officers), 4 time Global Infosec Awards Winner at RSAC2022 and has been recognized by a large number of other industry organizations and analysts.
